
AI
Cutting Through the Noise: Validated CTI Explained
Today’s cyber landscape, organizations aren’t short of data, they’re drowning in it. What leaders really need is trusted intelligence: knowledge that is validated, contextual, and actionable

AI
Today’s cyber landscape, organizations aren’t short of data, they’re drowning in it. What leaders really need is trusted intelligence: knowledge that is validated, contextual, and actionable

lidarkinesis
Turn noisy feeds into decisions your security program can live with.

AI
Amid noisy feeds and slow updates, analysts fall behind while execs see risk differently. LIDAR Kinesis centers the human: it collects intel, validates it, maps behaviors, and turns raw data into clear lessons, so analysts learn faster, leaders act, and tools run on verified CTI.
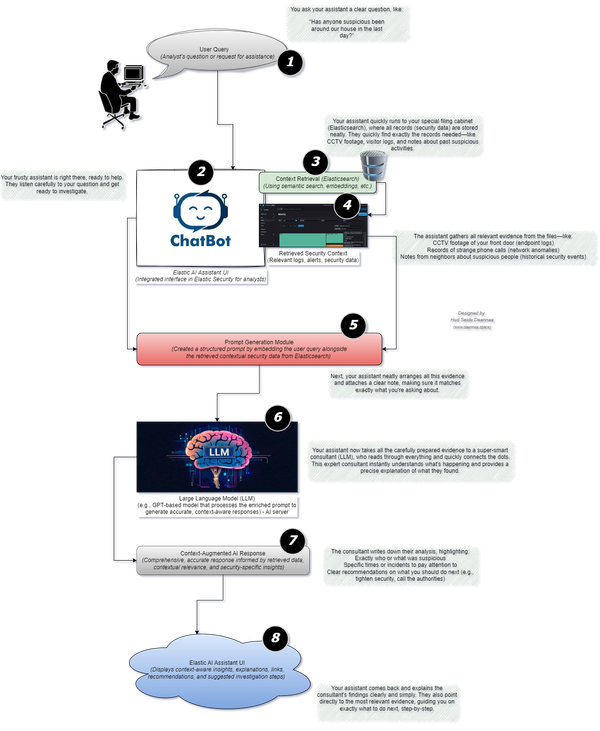
AI
Security analysts often must sift through massive volumes of logs, alerts and telemetry data. Identifying anomalies such as stealthy intrusions, lateral movement or data exfiltration can be time-consuming and error prone

AI
As smart devices quietly harvest our data, we risk losing control in an AI-driven world. Will technology propel us toward a future where humans evolve into humanoid robots, replacing broken parts like machinery? The choices we make today shape our tomorrow.
AI
As brain-computer interfaces and AI advance, the idea of downloading thoughts into computers blurs the line between human and machine. Could this lead to digital immortality, where humanoid robots inherit our consciousness? The quest for eternal life might soon be within reach.

AI
A structured cybersecurity reporting framework—linking assets, threats, CVEs, alerts, and incidents—empowers proactive threat management. By correlating data, it enhances situational awareness, incident response, and lays the foundation for AI-driven cybersecurity.

Today’s cyber landscape, organizations aren’t short of data, they’re drowning in it. What leaders really need is trusted intelligence: knowledge that is validated, contextual, and actionable

Turn noisy feeds into decisions your security program can live with.

Amid noisy feeds and slow updates, analysts fall behind while execs see risk differently. LIDAR Kinesis centers the human: it collects intel, validates it, maps behaviors, and turns raw data into clear lessons, so analysts learn faster, leaders act, and tools run on verified CTI.

Security analysts often must sift through massive volumes of logs, alerts and telemetry data. Identifying anomalies such as stealthy intrusions, lateral movement or data exfiltration can be time-consuming and error prone
Rabitanoor

Cyber Threat Intelligence (CTI) is essential in security operations, providing real-time insights on emerging threats. By integrating CTI, organizations enhance threat detection, reduce false positives, and align defenses with evolving adversary tactics.

Learn how cybersecurity analysts can use the cyber kill chain, Indicators of Compromise (IOCs), and AI to dissect attacks, recognize patterns, and create robust detection mechanisms, enhancing defenses against evolving threats.
AI tools like ChatGPT are transforming search, offering direct answers and intuitive conversations beyond traditional link-based results. As it gains traction, mastering ChatGPT may be essential, redefining how we find information in an AI-driven world

In the near future, with advances in VR and AI, we might spend as much time in virtual reality as we do on screens today. This could allow us to recreate the deceased, blurring the lines between virtual and real life, raising deep ethical and existential questions.

This framework shows how CTI enhances security by aligning with business objectives. It covers governance, asset categorization, and SOC operations, enabling proactive threat response through strategic, operational, and tactical intelligence.

As smart cities, IoT, and robots shape our future, the risks of cyber compromise loom large. Could these technologies become the battlegrounds of modern warfare? In a world dominated by AI, the fate of humanity depends on how we navigate these unprecedented challenges.

Data is the new oil of the digital age, shaping our choices, behaviors, and identities. It influences everything from personalized experiences to public policy. Understanding its origins, ownership, and the need for protection is crucial as we navigate this increasingly data-driven world.

CISOs often hesitate to embrace AI in cybersecurity due to fears of the unknown, potential vulnerabilities, and reliance on traditional methods. However, by investing in training, adopting a hybrid approach, and fostering innovation, they can unlock AI's transformative potential.

As electric vehicles (EVs) become mainstream, they raise critical privacy and security concerns. The extensive data collected—ranging from GPS location to driving habits—can be misused if accessed by unauthorized parties. Understanding these risks is essential as we navigate the digital road ahead.

In the evolving landscape of cybersecurity, understanding and anticipating threats requires a structured and comprehensive approach.

In the AI age, privacy matters more than ever. While AI search engines profile users, privacy-focused engines like RabitaNoor Search protect your data, ensuring confidential, trace-free browsing. For secure searches without tracking, explore RabitaNoor Search your privacy, guaranteed.

As Neuralink and AI technologies advance, the potential for creating cyborgs emerges, blending human capabilities with machine enhancements. This article explores the implications, benefits, and ethical considerations of merging human cognition with artificial intelligence.