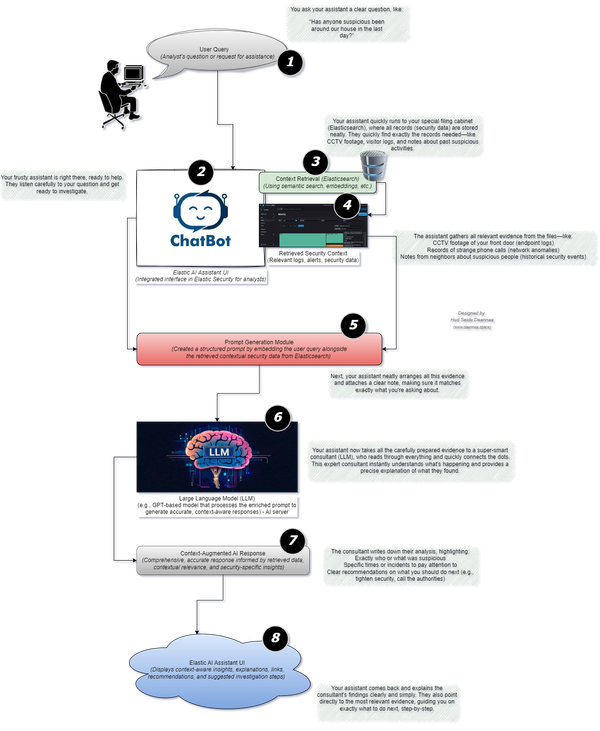
How a Correlated Cybersecurity Reporting Structure Paves the Way for an AI-Driven Defense Strategy
A structured cybersecurity reporting framework—linking assets, threats, CVEs, alerts, and incidents—empowers proactive threat management. By correlating data, it enhances situational awareness, incident response, and lays the foundation for AI-driven cybersecurity.

Today's digital landscape, where cyber threats continue to grow in sophistication and volume, organizations are seeking ways to improve their defenses and make informed, data-driven security decisions. A well-structured cybersecurity reporting framework is foundational to this goal. By correlating diverse data elements—such as assets, threats, vulnerabilities, detection rules, alerts, incidents, and forensic evidence—organizations gain comprehensive insights that not only support current security operations but also pave the way for an AI-driven cybersecurity strategy. This article explores the importance of a correlated reporting structure, the benefits it brings, and how it lays the groundwork for integrating artificial intelligence (AI) to enhance cybersecurity resilience.
The Goal of a Correlated Cybersecurity Reporting Structure
At its core, a cybersecurity reporting structure provides a systematic way to document, organize, and analyze key data elements related to an organization’s security posture. These elements include:
- Assets: Critical resources requiring protection.
- Threats: Potential sources of harm or compromise.
- CVEs (Common Vulnerabilities and Exposures): Cataloged security flaws relevant to the organization.
- Validated Vulnerabilities: Verified weaknesses that expose assets to threats.
- Detection Rules: Patterns that help identify suspicious activities.
- Alerts: Notifications triggered by detection rules.
- Incidents: Documented instances of confirmed security breaches or attacks.
- Forensic Evidence: Data artifacts for investigating incidents.
By correlating these elements, organizations can build a cohesive and actionable view of their cybersecurity landscape. This correlation supports risk assessment, incident response, and continuous improvement, ensuring that cybersecurity measures align with business objectives.
Correlating Elements within the Reporting Structure
A correlated reporting structure brings together various elements to provide context and insight, enhancing each element's contribution to overall security. Here’s how the key components relate to each other:
-
Assets and Threats: Assets define what needs protection, while threats indicate potential risks. By linking assets with specific threats, security teams can focus protection efforts on high-risk areas and tailor detection and response measures to the specific risks associated with each asset.
-
CVEs and Validated Vulnerabilities: CVEs are known vulnerabilities, but not all are relevant to every organization. Validated vulnerabilities are specific to the organization’s environment, and correlating these with CVEs allows teams to prioritize which vulnerabilities need urgent attention based on both external intelligence and internal conditions.
-
Detection Rules and Alerts: Detection rules outline suspicious patterns, and alerts are generated when these rules are triggered. By continuously refining detection rules based on insights from past alerts and incidents, the reporting structure minimizes false positives and enhances the accuracy of threat detection.
-
Incidents and Forensic Evidence: Incidents are security breaches or malicious events, while forensic evidence provides the data necessary for investigating these incidents. Correlating incidents with forensic evidence supports thorough incident analysis, helping the organization trace attack sources, understand impacts, and improve future defenses.
Through this correlation, the reporting structure provides a holistic view of security operations, where each component informs and strengthens the others. This connected approach drives more effective threat management, incident response, and long-term resilience.
Benefits of a Correlated Reporting Structure
The advantages of a correlated reporting structure extend beyond basic record-keeping. When data elements are linked in meaningful ways, organizations experience tangible improvements in cybersecurity effectiveness. Key benefits include:
-
Improved Situational Awareness: Correlating threats, vulnerabilities, and incidents enhances situational awareness, providing a clear, comprehensive view of the organization’s risk landscape. This insight enables security teams to prioritize efforts and proactively defend against likely attack vectors.
-
Faster, More Effective Incident Response: A correlated structure allows teams to quickly assess and respond to incidents, understanding their origins and impacts. This speed and efficiency minimize the potential damage of a breach and enable faster recovery.
-
Enhanced Threat Intelligence: External intelligence (e.g., new CVEs and threat actor data) becomes more actionable when correlated with internal vulnerabilities and incidents. This tailored intelligence empowers security teams to implement precise, proactive defenses.
-
Resource Optimization and Cost Efficiency: A correlated reporting structure allows teams to focus on high-priority issues, eliminating redundant efforts. CVEs irrelevant to the organization’s validated vulnerabilities can be deprioritized, saving time and resources.
-
Support for Compliance and Risk Management: Correlating incidents, vulnerabilities, and forensic evidence provides a clear audit trail, which is essential for regulatory compliance and risk management. This structured documentation demonstrates a responsible approach to managing cyber risks and enables smoother audit processes.
How a Correlated Reporting Structure Enables AI-Driven Cybersecurity
A structured, correlated reporting system is the foundation for building an AI-driven cybersecurity program. By systematically collecting and organizing data on assets, threats, vulnerabilities, and incidents, organizations create a rich dataset that can drive AI-powered insights and automation. Here’s how:
-
Training Data for AI Models: The structured data provided by the reporting system offers a solid foundation for training AI models. Patterns in threat behaviors, common vulnerabilities, and detection rules can be used to build models that enhance detection capabilities, recognizing correlations and anomalies that may be missed by human analysts.
-
Automated Threat Detection and Response: An AI system trained on correlated data can automate threat detection and response by continuously analyzing assets, threats, and detection rules. By learning from past incidents and forensic evidence, AI can detect and respond to threats with greater speed and accuracy, often in real-time.
-
Enhanced Threat Intelligence and Proactive Defense: AI can leverage external and internal intelligence, correlating global CVE data and threat trends with the organization’s specific vulnerabilities and assets. This real-time correlation allows AI to recommend security patches, adjust detection rules, and predict attacks based on emerging threats.
-
Predictive Analytics for Risk Forecasting: AI can perform predictive analytics using the organization’s data, forecasting potential risks and vulnerabilities before they are exploited. By analyzing trends in CVEs, threat actors, and past incidents, AI can help security teams fortify defenses against anticipated threats.
-
Anomaly Detection and Behavioral Analysis: Access to comprehensive data on past alerts, detection rules, and forensic evidence allows AI to establish baseline behaviors for assets and users. This baseline enables AI to detect anomalies that might indicate malicious activity, helping the organization to detect subtle threats that would otherwise go unnoticed.
-
Continuous Learning and Adaptation: As new data flows into the reporting structure through incidents, CVEs, and threat intelligence, AI systems can learn and adapt dynamically. This capability enables organizations to maintain a defense posture that evolves with the threat landscape.
-
Enhanced Decision-Making Support: By analyzing data correlations, AI can provide actionable recommendations for security teams, facilitating faster, data-driven decisions without the need for manual analysis.
Conclusion
In an era of increasing cyber complexity, a correlated cybersecurity reporting structure is indispensable for organizations aiming to stay ahead of threats. By organizing and linking critical elements—assets, threats, CVEs, validated vulnerabilities, detection rules, alerts, incidents, and forensic evidence—organizations gain a comprehensive view of their security landscape. This structure not only supports efficient risk management and compliance but also enhances situational awareness, incident response, and threat intelligence.
Furthermore, a structured reporting system provides a rich dataset for training AI models, enabling organizations to build AI-driven cybersecurity programs that are predictive, adaptive, and efficient. With AI’s capability to analyze patterns, detect anomalies, and forecast potential threats, organizations can transform cybersecurity from a reactive discipline into a proactive, intelligent defense mechanism.
The integration of AI into cybersecurity is no longer a vision of the future; it is a necessary evolution. By establishing a solid reporting foundation, organizations can unlock the full potential of AI to protect their most valuable assets, ensuring resilience and alignment with business objectives in an increasingly digital world.
References
- MITRE Corporation. (n.d.). MITRE ATT&CK® Framework. Retrieved from https://attack.mitre.org.
- Ponemon Institute. (2023). The Value of Correlated Data in Cybersecurity. Ponemon Institute Report.
- Gartner. (2022). How AI is Transforming Cybersecurity Operations. Gartner Research Report.
- NIST. (2022). Framework for Improving Critical Infrastructure Cybersecurity. National Institute of Standards and Technology.
- Kaspersky Labs. (2021). Leveraging Artificial Intelligence in Cyber Threat Intelligence. Kaspersky Whitepaper.